mGramSeva iFIX Adapter Service
Overview
Ifix-Adapter is a system that works as a mediator between iFIX and its clients. This system will receive requests from the client system and convert the data in the iFIX required format This document contains the details on how to set up the iFIX-adapter service and describes the functionalities it supports. It supports multiple events (Event Array) in a single request.
Pre-requisites
Before you proceed with the configuration, make sure the following pre-requisites are met -
Java 8
The Kafka server is up and running
The PSQL server is running
Redis
The following services should be up and running:
Client Service Like mgramseva-ifix-adapter
Target service IFIX- fiscal-event-service
Target Service IFIX-keycloak
Adapter master data service
Key Functionalities
IFIX client requests are pushed to IFIX.
The authentication token is fetched from keycloak and cached. Token is re-fetched 5 minutes before expiry.
project_id from request data is getting treated as Department Entity Code to fetch Department Entity.
COA Code fetched from COA Mapping table by client code and cached it in Redis Server.
Every push to IFIX is recorded in the table with HTTP status
status series 200 considered success
status 400 are marked client error
It collects projectId form request data, treats it as department_entity_code and calls search API to Department Entity Service. It always expects it will receive only one Department Entity against a single department_entity_code, if it finds multiple raises an error message.
One project can have multiple department entities but vice-versa cannot be true. In case of multiple projects for one department entity - the system will raise an error message.
Deployment Details
Deploy the latest version of the ifix-reference-adapter.
kafka.topics.ifix.adaptor.mapper
Topic in which client requests are put. From this further listen and posting happens
keycloak.host
Host name of the key cloak authentication token provider
keycloak.token.url
key cloak authentication token url
keycloak.credentials.clientid
userid of for authentication token
keycloak.credentials.clientsecret
password for authentication token
ifix.host
host name of IFIX server
ifix.event.url
IFIX post URL
spring.redis.host
Host name of the redis server
state.goverment.code
top level tenant id of the client
spring.jpa.properties.hibernate.dialect
dialect for JPA. you can change this to oracle or my sql etc
spring.jpa.properties.hibernate.jdbc.lob.non_contextual_creation
will generate the required tables in the respective database . This feature is used instead of flyway to get database in-dependency
Configuration Details
Map clientcode, ifixcoacode, ifixid in ifix_adapter_coa_map table
“clientcode” is the tax head like “WATER_CHARGES” or ‘10011’ used in IFIX clients like mgramseva
“ifixcoacode” is the 16 digit glcode in IFIX. 16-digit code is mapped then this can be ported to any environment like dev to qa, or qa to uat or from uat to prod. Prefer mapping ifixcoacode
an example is INSERT INTO public.ifix_adapter_coa_map(id, clientcode, ifixcoacode, ifixid, tenantid) VALUES (1,'10101', '0215-01-102-00-00-01', '6cbcb4a1-2431-4f78-89d7-b4f0565aba37', 'pb');
state.goverment.codeset this value to the client top level tenant_id
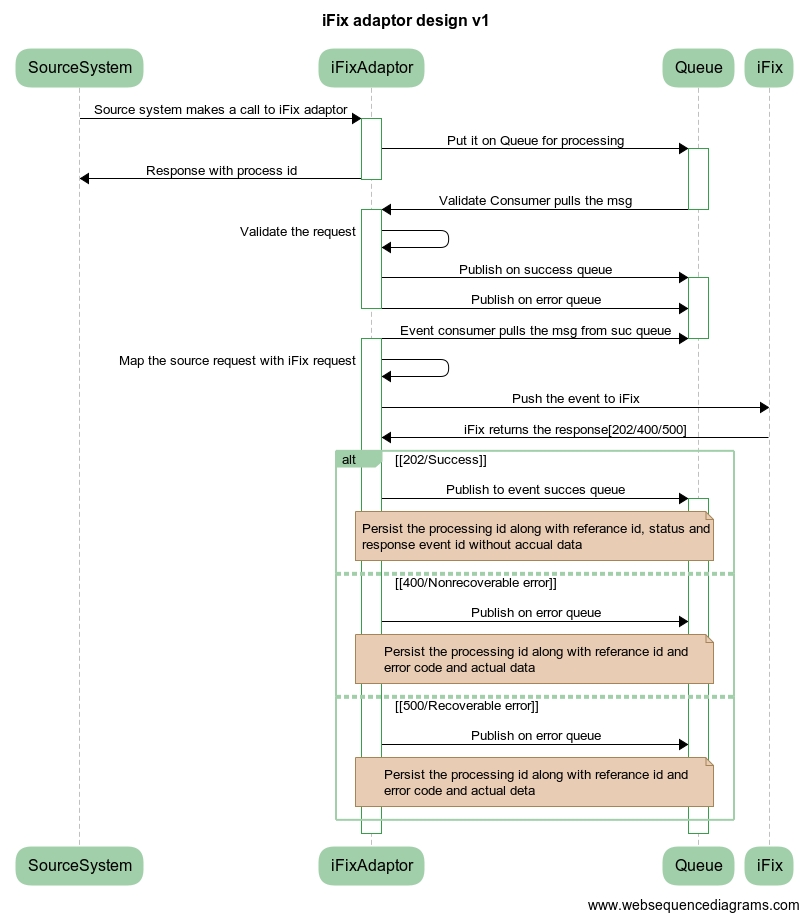
Interaction Diagram
Reference Docs
Doc Links
API Swagger document
API List
events/v1/_push
API for receiving data from client (mgram). This is the only API present in the adapter
Last updated
Was this helpful?